Zero Trust Segmentation
Eliminate lateral movement, even on the LAN with per-device microsegmentation at the network level.
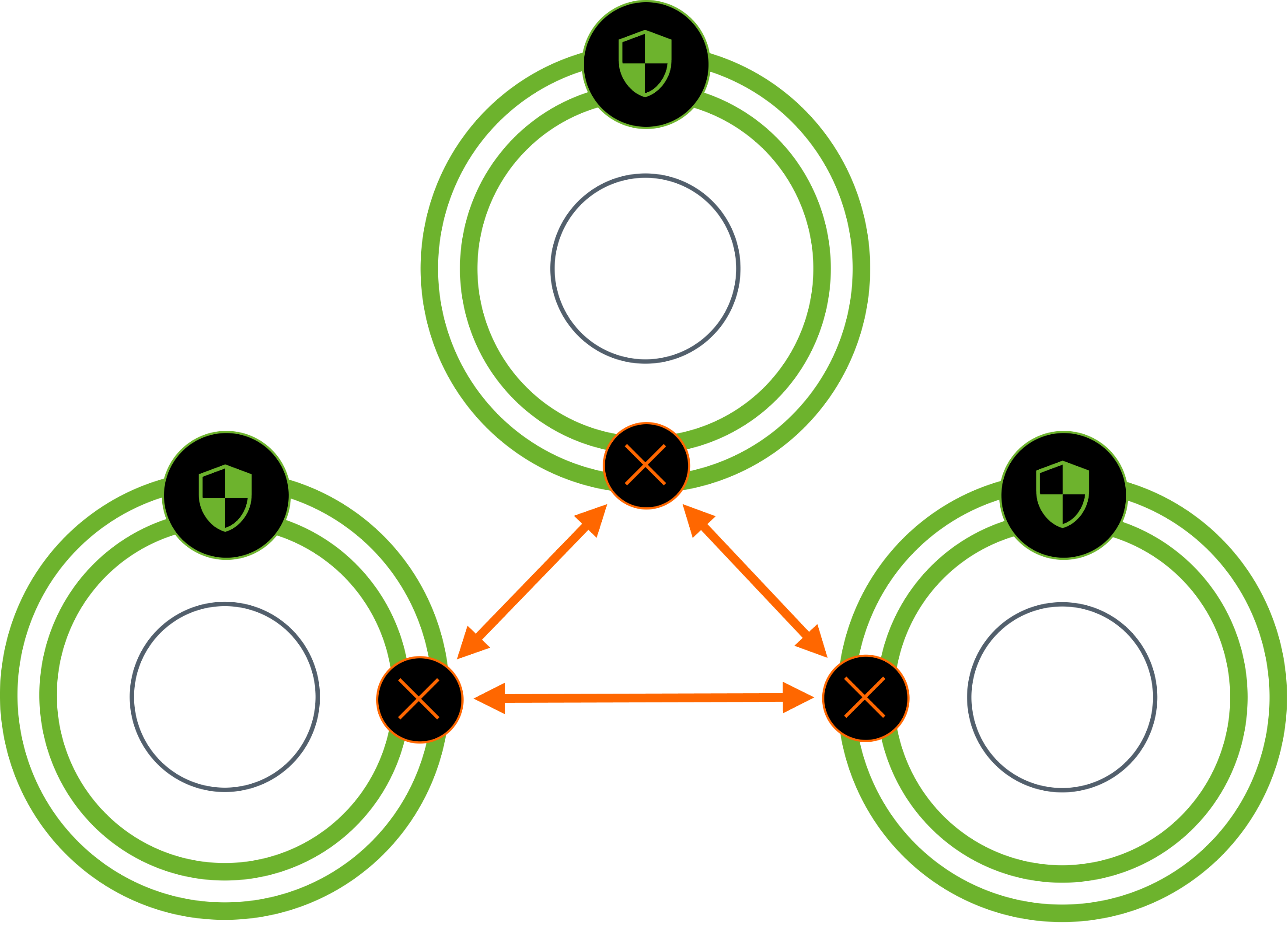
Designed to prevent devices from communicating with each other, ready for when they get compromised.
Whether you're protecting a branch office, an industrial site or a core datacentre, Zero Trust Segmentation gives you hard guarantees on isolation and access without traditional VLANs or complex overlays.
Prevent lateral flow
At its core, Evolving Zero Trust Segmentation embraces and enforces Zero Trust thinking by assuming every device on the LAN is a potential attack vector.
No trusted versus untrusted networks – everything is untrusted.
Zero broadcast domains. Zero flat LANs.
It applies Zero Trust principles right where traditional segmentation fails – inside the so called "trusted" LAN.
The result is a clean, tight segmentation model that works out-of-the-box and scales easily across branches, sites or embedded environments.
What it does
At its core, Evolving Zero Trust Segmentation:
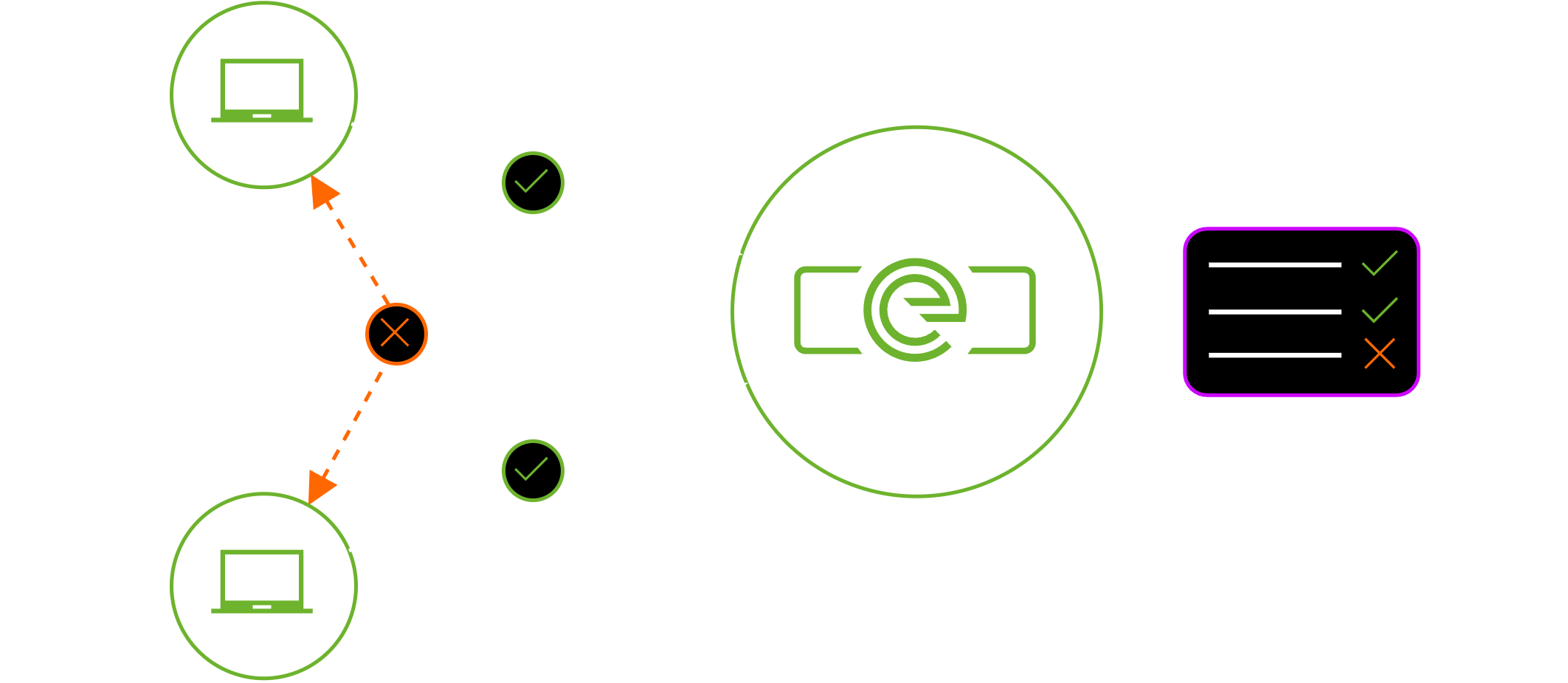
Assigns every device a /32 IP address
Implements strict, default-deny policies at the EVX gateway
Blocks all lateral east-west traffic by default
Enforces identity- and policy-based exceptions only as needed
Why it's different
Traditional segmentation methods – VLANs, zones, static firewall rules – were not designed for the speed, scale, or complexity of modern access models.
A full NAC system involves huge disruption and integration between all of the LAN hardware. Zero Trust Segmentation solves that.
Banish outdated topologies
Hub-and-spoke and full-mesh are not fit for purpose in a Zero Trust world.
Traditional LAN networking is a free for all. The hub-and-spoke and full-mesh topology default of "any to any" has left us with significant conceptual debt.
Zero Trust needs a radical rethink of the standard LAN and WAN topologies. One where up-and-out becomes the default, and zero peer the norm.

Part of ZERO SDWAN. Powerful on Its Own.
Zero Trust Segmentation is a standalone service, but it also forms the foundation of ZERO SDWAN. Within the SDWAN context, it allows:
Per-site, per-user, or per-flow dynamic path control
Safe onramp to mesh connectivity, with identity-based segmentation preserved
Segmentation-aware routing decisions (e.g., deny WAN breakout for isolated devices)
Easy to deploy. Hard to breach.
You don’t need to rearchitect your LAN. Drop in an EVX running Zero Trust Segmentation and the following happens automatically:
All devices get isolated by default
No lateral movement between endpoints
Admins can apply exceptions based on policy
Enforcement is transparent and deterministic
From the moment a device receives an IP, it’s ringfenced.
Get connected
Request a free call with our network experts to find out more.
Trusted by




















